The internet is more far reaching than most realize. It is estimated that there is 500 times more content on the internet than what can be found on google. This is not because all this content is dangerous or illegal. Most of it is actually just not public or not relevant to the user, so search engines don't index it. This can include email messages, private content on social media, bank statements, health records. Much of this is reachable, just not through your standard search engine. If you ever used J-Store in college to find articles, then you have used a search engine that can find the things google cannot. Regardless, this breadth of resources is known as the deep web. The web most people know and use is conversely titled the surface web. That is not all there is on the deep web though. There is a small slice kept away and not accessible by any standard means. This place, known as the Dark Web, is home to marketplaces for drugs, weapons, fake ids, and other illicit items. If you have ever heard of the fabled Silk Road, now you know where it was located. Illegal substances aren't the only things permeating the Dark Web. It can also be a means to anonymize your online surfing. This article will show you how to get into the dark web. What you do from there is up to you.
First Thing's First, Tor

The Dark Web is hosted on servers around the world. To access these servers, you will need the Tor browser. Tor is short for The Onion Router. Why Onion? Well, it's because Tor is like an onion; it has layers. Specifically, Tor has layers of protection to ensure your anonymity. Websites only available on the Dark Web end with the domain “.onion.” The best way to learn more about what Tor does on the back end to keep your IP hidden is to visit their site. This is also the only place you should be downloading the Tor browser from. Once installed you now have Tor on your computer and you can begin exploring the dark web. It will mask your IP to prevent you from being traced or monitored. Other features you have to expect from your browser, like javascript, will be disabled as they would threaten your newfound privacy. It is advised that you familiarize yourself with all the settings and features before exploring. While Tor will block your ISP from seeing where you go and what you do, it will not prevent them from seeing you are on Tor. This is something to be concerned with, especially if you are looking to use Tor for less than legal purposes. A ruling in 2016 by the supreme court granted the FBI the ability to search and seize any computer using Tor under probable cause. The best way to combat this is by downloading a VPN.
VPNs and Privacy
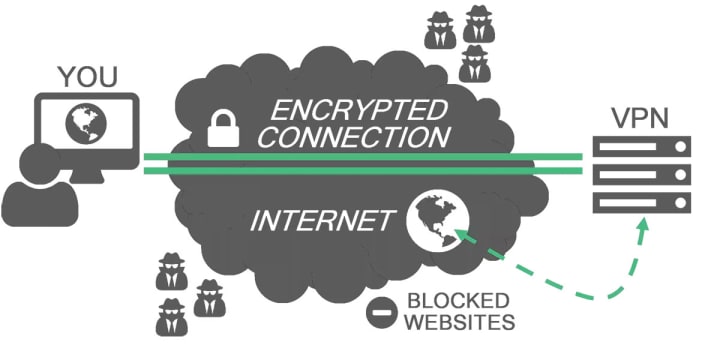
A VPN, or Virtual Private Network, allows you to gain another level of privacy when using the internet by encrypting the data and sending it to a server in another location. This gives the illusion that the user is using the internet from this new location. VPNs are commonly used to get around regional restrictions to sites like Netflix. Using a VPN in conjunction with Tor will prevent ISPs from seeing anything other than your encrypted VPN traffic. Then the only way your use of Tor can be traced back to you is from the VPN if it keeps logs. As such you should look for a VPN that keeps you the most anonymous.
When using a VPN with Tor, it is important to consider how the two interact. "Tor over VPN" means you connect to your VPN server then open Tor. Your internet traffic is encrypted by the VPN then sent to Tor which works its magic. This method hides your use of Tor from the ISPs. Alternatively, "VPN over Tor" encrypts your data from Tor nodes through your VPN which is then routed to the internet. This means your VPN provider will not see that you are on Tor, preventing them from logging your use of Tor. This will also prevent your ISP from knowing you are using a VPN but will alert them to the fact that you are using Tor. There are benefits to each but Tor recommends Tor over VPN and only a handful of VPNs even support the alternative. Either way, you should be using a VPN when using Tor.
Where to Go, What to Do

Now that you know how to get into the dark web, you can finally begin exploring. The best place to start is the hidden wiki. You can reach this a few ways. The surface web hidden wiki site will offer a link to get there as will searching for the hidden wiki in one of the Tor search engines. This is a great launching point for all your needs. DuckDuckGo is one of the better search engines you can use. Unlike Google, it does not track you or record your information. Grams is essentially the google of drugs. Be warned, there are many links that can be quite depraved and you should be cognizant of where you are going. Tor can be used to enter normal sites as well though it handles them differently and runs different risks. One of the primary purposes of .onion sites is that they are designed to not have the same weaknesses that other sites have. This, along with other factors, plays into why many of the sites seem more visually simplistic.
Last Things Last; Tor Relays and Safety

As stated, Tor handles normal websites differently from hidden sites. Tor automatically relays your requests from normal sites through nodes. Nodes receive encrypted traffic and pass them on. These nodes are operated by various individuals and groups around the world. The more relays in use, the faster and safer Tor will be. All traffic passes through at least three nodes and there are three types of nodes. The first two nodes are always Middle Nodes. These nodes simply receive traffic and pass it along. While these nodes are listed so they can be connected to they are anonymous. Bridges are similar to middle nodes but are not listed as part of their network. They are useful for circumventing censorship in areas that block publicly listed middle nodes. Lastly, exit nodes are the final relay traffic passes through before reaching its destination. The exit relay decrypts the traffic so the user can finally reach the site or destination. As such, the exit relay appears as the source of the traffic. Because the exit node decrypts the traffic, its creator can see what you are accessing. Some exit nodes are thus used by malicious people to find your identity. But fear not! Tor accounts for much of this and does not use known bad nodes. There are steps you can take to ensure your anonymity anyway.
For one, make sure the sites you go on use HTTPS. This makes your communications encrypted, so any bad nodes would still deal with the encrypted settings. As Tor is for high-level anonymity, I advise you attempt to remain anonymous when using Tor. That means do not use sites that acknowledge your identity. So no Facebook, Twitter, Reddit or sites that can be traced back to you. You should also stick to untraceable currencies like Bitcoin when making any purchases. Knowing how to get into the Dark Web is only the beginning of the journey. Becoming part of this community means always doing research and learning more about Tor and the Dark Web. Good luck, and happy browsing.



No comments yet
Be the first to share your thoughts!